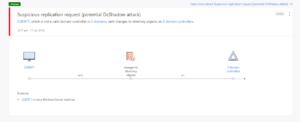
CyberSecurity is a never-end journey. The good old games are the same, old, always here and never outdated. As an old arcade games fanboy and an actual CyberSecurity & IAM expert, it is amazing to see how the old rules serve the current war against malware, lack of systems configuration and black hats.
Let’s review the rules and remember the happy days.
Rule 1 with Space Invaders: hide yourself behind a wall is not enough for a good defense strategy
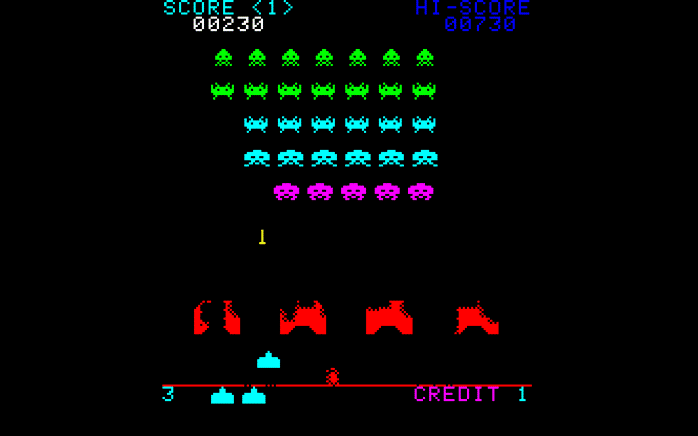
In the Space Invaders game, you can stay behind the red wall, you will live for 5 minutes, but at the end you will die. Against the threats, is not enough to hide yourself and think the better days are coming. In an open world, you will need to build a defense strategy beyond an unique firewall strategy. The perimetric security is dead, you need to use other strategies. It doesn’t mean you don’t need a firewall or several, but you can’t think is enough to protect your network. Build a security data strategy, an encryption strategy, an authentication strategy and all the important strategies you need.
Rule 2 with Donkey Kong: The lateral movement will provide privileges escalation for the attacker
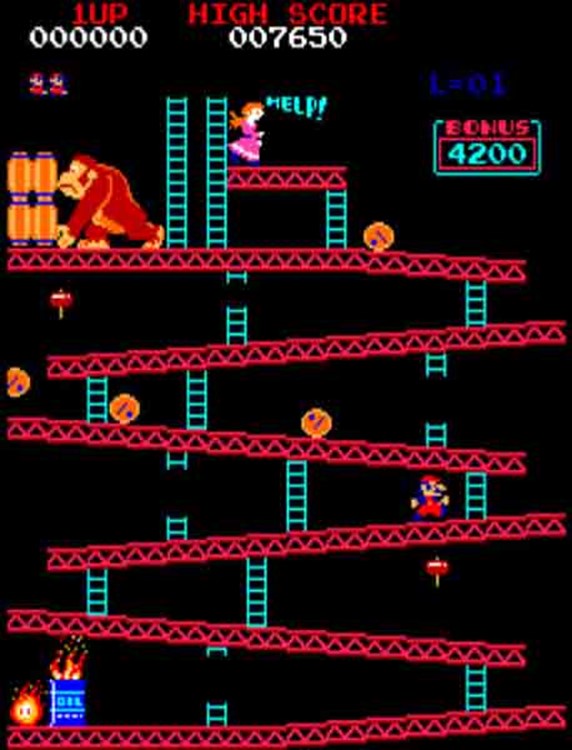
In the Donkey Kong game, you will learn to do horizontal movement or vertical movement at the exact instant you need to. This is very true, especially when we are talking about Active Directory Hardening. The attacker will not try to catch the top-level system first, he will first try to compromise one workstation, and then he will try to go horizontal and get access to the other workstations. He will look for some high-level account privilege traces on the workstations. As soon he finds it, he is ready and now it is time to go vertical, climb the systems and go to the holly Graal, the Domain Controller of Active Directory.
Rule 3 with Spy vs Spy: Using some HoneyPots is always a good strategy
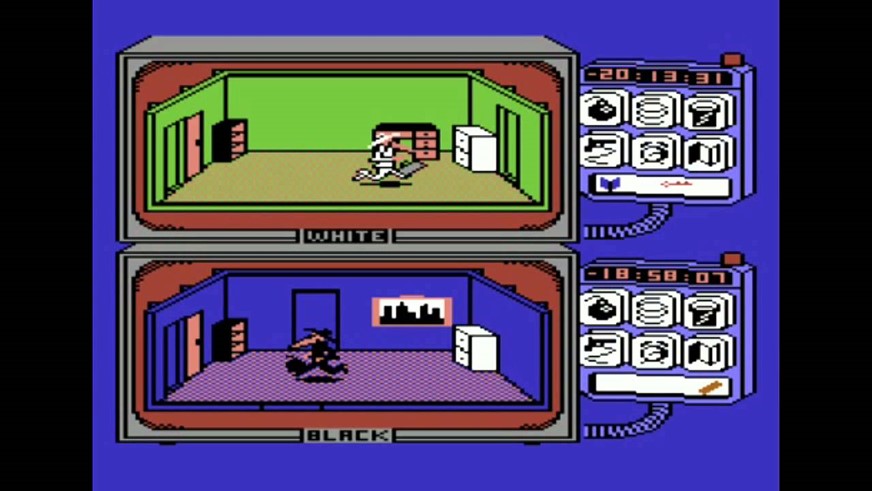
In the Spy vs Spy game, the better way to defeat your adversary is to create and put some traps. When you want to detect the attacker, deploy some honeypots on your network will provide a good way to catch him. You can use honeypot in different manner: fake web site, fake DNS entries, fake admin accounts, etc. The only challenge will be to have a good understanding of the way the attacker acts to be sure you will put something interesting for him.
Rule 4 with 1942: Agility and movement are key if you want to succeed against the enemy

In the 1942 game, if you stay at the same place on the screen you are dead after 2 seconds. When you are in movement, it is difficult to catch you. You need to constantly move and get agility to improve your faculty against the attacker. Don’t be static, change the configurations, change the passwords, change the different tools you are using to implement you defense. Evaluate new solutions, invent new defense – in one word, be Agile.
Rule 5 with Double Dragon: Yes, you can beat a boss bigger than you

In the Double Dragon game, you will destroy a boss in every stage, each boss is bigger and more powerful than you. Even if the adversary seems to be huge: well-trained, large experience with good technical skills, you can beat it. It is matter for anticipation, pugnacity and strategy. You can defeat the beast, but you need to study the beast strategy, learn the way he moves, learn the way he acts, learn his characteristics and you will be able to succeed.
Rule 6 with Sorcery: Each system owns a specific weakness
In the Sorcery game, each object will kill a specific creature: The Strong Sword kills the monks, the Sharp Axe kills the ghosts, the ball & chain kills the Beholder, etc. Sometimes you are not responsible of the system or application choice, but you need to protect it. Here it is difficult, because you are not a specialist on every system, but you will need to study and learn about the different key weakness for each: Windows, Linux, Oracle, Tomcat, etc. have specific issues or weakness -So you will need to train yourself, speak with other specialist and define the correct strategy for each system. It is hard, time consuming but you will get a basic understanding on all the platforms you need to protect.
Rule 7 with Ghosts’N Goblins: Practice, practice and again practice
In the Ghosts’N Goblins game, the first 50 times you will play the game, you will die very quickly, after a while you will start to succeed in the game. You need to train & practice – again, train & practice – again, train & practice – etc. As you understand, this is again a never end story, you always have new technologies, new type of attack, new discovered vulnerability – the only way to make a good job for you in terms of security is practice and practice again. Your self-training capabilities will be key in your success. Again it is time consuming, but you will get a very good ROI from your tests and labs.
Rule 8 with Golden Axe: Different people, different skills, you need to build a strong team for defense

In the Golden Axe game, you must use different type of characters which have different skills considering the situation and your enemy. You can’t perform everything by yourself, you can’t be a top specialist on every technology or system. So, you need a team, a strong defend team with various people who have different technology knowledges. With a good mix of folks, which complete each other, you be able to succeed against the threat.
Rule 9 with OutRun: Speed is your best friend and speed is your best enemy

In the OutRun game, if you go too slow you will lose the race, if you go too fast, you will break your car in a wall. For sure, when you are under attack, you will need to react very fast to get the systems back and be safe again – BUT – sometimes if you react too fast you will make the wrong choices, in fact you need to find the good tempo. You are under attack ? take a good breathe, a strong coffee, a fine whisky and think about it, you will need to investigate the situation before to react and find the prefect planning to fix the breach. Be fast, don’t be too fast.
Rule 10 with Tetris: Build your own pattern
Tetris is my FAVORITE game. I played during hours, days, weeks, months when I was younger. The very important teaching with Tetris is you will have different way to win the game. Depending your personality, you will play a different way. It is not existing a good or a bad way to play, the good way is only the way which permits you to win the game. It will be the same with your defense strategy, depending who you are, depending your skills or your personality, you will elaborate a different strategy. Know your systems, know yourself and build your own pattern.
Remember the rules:
Rule 1 with Space Invaders: hide yourself behind a wall is not enough for a good defense strategy
Rule 2 with Donkey Kong: The lateral movement will provide privileges escalation for the attacker
Rule 3 with Spy vs Spy: Using some Honey Pot is always a good strategy
Rule 4 with 1942: Agility and movement are key if you want to succeed against the enemy
Rule 5 with Double Dragon: Yes, you can beat a boss bigger than you
Rule 6 with Sorcery: Each system owns a specific weakness
Rule 7 with Ghosts’N Goblins: Practice, practice and again practice
Rule 8 with Golden Axe: Different people, different skills, you need to build a strong team for defense
Rule 9 with OutRun: Speed is your best friend and speed is your best enemy
Rule 10 with Tetris: Build your own pattern
, and thanks to the old arcade games !